Description of work
The 5G-INSIGHT project is organized into 7 work-packages as follows:
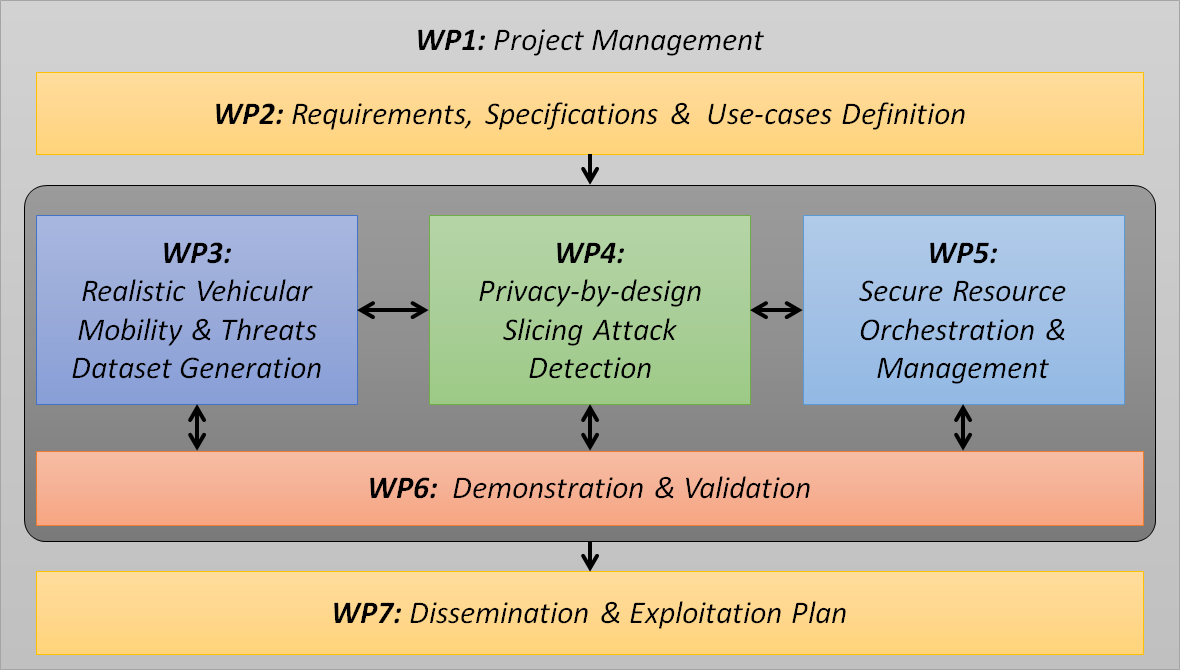
- Work Package 1: Project Management :
The aim of this work package is to provide overall management, including administrative, operational, and financial aspects of the project. It covers all the management activities and provides and maintains the link to the national funding agencies. It coordinates the project towards achieving the targeted goal and objectives. - Work Package 2: Requirements, Specifications, & uses-cases Definition :
The main objective of this work package is to: (i) provide detailed scenario definitions covering three main use cases, (ii) underline network vulnerabilities, its targeting attacks and cyber threats, and (iii) analyse requirements and derive specifications for system model design. A strong emphasis will be put on technical details and relevant research works in 5G and vehicular networks security challenges. The expected outcome would be a detailed definition of vulnerabilities and threat models along with detailed scenario definitions. The resulting deliverables will provide a clearer understanding of the underlying challenges and will be the cornerstones for the following WPs and the rest of the project. - Work Package 3: Realistic vehicular mobility and threats dataset generation:
The aim of this WP is to collect and generate realistic datasets representative of cross-border environments, which will then be used to develop the required ML models for attack detection in WP4. A mapping between three types of data will be carried out, namely: mobility and network data, as well the threats identified in WP2. Three complementary objectives are foreseen: 1. Collect realistic datasets via the French platform "TransPolis", which will physically reproduce part of the scenarios described in WP2. 2. Generalize these datasets with simulation tools and prediction techniques so that they can be generalised and scaled-up to any type of behaviour in a cross-border area (e.g. presence of many vehicles, unstable network traffic). 3. Propose supervised learning techniques to predict mobility and network behaviors that can lead to the threats identified in WP2, and subsequently attach labeled data to the datasets generated in (2). This WP takes as an input all the specifications defined in WP2 and serves as input to the other WPs, which are at a more specific level of the project's technical architecture. Ultimately, this WP will provide the necessary datasets and indicators for the selection of mitigation strategies in the next WPs. - Work Package 4: Privacy-by-design slicing attack detection :
This WP will design and develop ML-based models to detect V2X slicing attacks by exploiting the datasets generated in WP3. Our objectives are twofold: (i) design and development of accurate ML-based models for early detection of single source attacks; and (ii) design and development of a federated learning approach to detect multiple-source attacks, while preserving slices privacy in both classical and roaming scenarios. - Work Package 5: Secure resource orchestration and management :
This WP addresses response and mitigation following each type of attack identified by the detection algorithms developed in WP4. Different kinds of countermeasure actions are proposed here and range from developing specific mitigation algorithms to overcome identified attacks, to their instantiation and deployment within the network itself as virtual network functions (VNF). Offering the means to ensure user’s privacy preservation and privacy data accountability in the process of ML-based attack detection, developed in WP4, is also one of the objectives of this WP. - Work Package 6: Demonstration and validation :
The aim of this work package is to validate our 5G-INSIGHT approach by building a secure 5G vehicular testbed in a Lab environment first, integrating it with a Security Information and Event Management (SIEM) open source solution, and then export it within a real automotive platform, called TransPolis [4], developed by UGE in cooperation with Ifsttar. Anomaly detection algorithms developed in WP4, and mitigation agents developed in WP5 will also be integrated in our demonstration platform. - Work Package 7: Dissemination and exploitation plan :
This WP aims to build a strategic plan for dissemination of the results, creation of contact with possible stakeholders in order to deploy a new service, creation of synergies with other projects, publications, etc. The main objectives of this WP are: (i) diffuse scientific and technical knowledge generated during the project through a set of dissemination activities, (ii) raise end users’ awareness and attract potential supporters amongst interested operators/vendors through a tailored communication strategy, and (iii) understand the existing market and identify prospects in order to formulate a feasible marketing strategy and a business plan for potential stakeholders.
